CyberArk Tutorial for Beginners
We sincerely appreciate your time, and we thank you everyone for visiting. View the CyberArk Beginners Tutorial or go to CyberArk Training to learn everything there is to know about the CyberArk and how it may help you as a beginner.
CyberArk Meaning

It’s a privately held cybersecurity company known as CyberArk provides businesses with on-premise software solutions designed to safeguard sensitive information and accounts, from Password Protection and internal and external attacks, through on-demand software solutions created by CyberArk.
By taking advantage of CyberArk solutions businesses can improve security risk management while cutting IT costs while increasing operational efficiencies simultaneously, these solutions from CyberArk can even be deployed remotely into cloud systems!
It was first released for sale to customers worldwide in 2002. Since then, their software has attracted over 2,000 clients globally – becoming one of the premier solutions available worldwide to ensure secure accounts and data for privileged accounts and private data access.
It provides targeted assault protection, ransomware detection solutions as well as insider threat defense for organizations looking to shield their most critical networks and data against external and internal attackers alike.
CyberArk’s Privileged Account Security Solution, as the cornerstone of its software, seeks to minimize organizations’ attack surfaces and vulnerabilities against criminal actors by offering strong platforms for identification, privilege access management and password administration, additionally it can assist organizations with auditing secret accounts and credentials.
CyberArk software also boasts vaulted identity management features that help businesses manage User Authentication and Password Administration using just one tool.
It provides businesses that require assistance complying with various rules with access to expert services that include risk management and cyber security advice as well as customized solutions tailored specifically for each organization’s individual requirements.
CyberArk Cloud Integration
Cloud integration refers to the process of linking cloud services, apps, data and infrastructure together to allow processes and operations across various cloud services. CyberArk offers businesses a cloud integration service which gives them secure data access as well as capabilities necessary for using company resources within the cloud safely.
Businesses today can utilize various cloud services, including Infrastructure-as-a-Service (IaaS) and Software-as-a-Service (SaaS), with CyberArk’s enterprise security solution providing more protection and control over these apps and cloud services, including their access and management privileged cloud services safely with total protection solutions provided by CyberArk.
Organizations can safely store login, authentication and access keys with CyberArk Cloud Security and Access Layer (CASL), an additional layer of cloud application security.
It helps organizations Protect Data Loss, Unauthorized Access and Malicious Activities by segregating privileged accounts from company networks, additionally it links up with current infrastructure for managing secret accounts to give clients a comprehensive approach to cloud protection.
It also provides a cloud access control solution, making it simple for businesses to sign up and manage various cloud services and applications.
Companies using CyberArk’s solution can quickly audit user activities while tracking access privileges across applications and services.
Companies facing digital transformation must prepare to protect sensitive data, infrastructure and applications with market-leading comprehensive security solutions such as CyberArk’s market-leading comprehensive security solutions, helping businesses recognize, monitor and control user access across applications used internally, protecting systems against authorities’ access through CyberArk Integrations.
It provides organizations with solutions for meeting the security needs of their clients securely. Their advanced security products enable businesses to manage privileges across platforms while consolidating them seamlessly for effective administration.

CyberArk offers its clients various authentication techniques, Single Sign-on, Biometrics and Multi-Factor, in order to enhance security.
This enables users to be securely identified while also controlling access to software or information in a regulated fashion.
CyberArk pam tutorial
CyberArk PAM protects organizations against data loss, disruption, cyberattacks and any other form of malfeasance. By employing its automated solution to better monitor privileged access and regulate it, businesses can ensure protection of sensitive data and systems against loss or misappropriation.
It helps organizations mitigate organizational risk by dramatically decreasing insider assault risks, prompt resolving privilege issues and immediately detect when accounts have been compromised.
Furthermore, it automates provisioning, revoking and overseeing of privileged access for confidential systems as well as mission critical systems by giving individuals appropriate rights and permissions.
It helps businesses meet both legal and auditing obligations efficiently. It facilitates easier with auditing requirements by automating recording access of privileged accounts to sensitive data, applications, and systems while assuring only authorized transactions use secret accounts for processing operations.
CyberArk Aim Integration
 CyberArk’s Aim Integration platform utilizes Predictive Analytics and Machine Learning technology to quickly detect any suspicious or malicious activities in privileged accounts, helping organizations centrally manage and govern secret accounts thanks to integrations with leading collaboration, identification and security solutions.
CyberArk’s Aim Integration platform utilizes Predictive Analytics and Machine Learning technology to quickly detect any suspicious or malicious activities in privileged accounts, helping organizations centrally manage and govern secret accounts thanks to integrations with leading collaboration, identification and security solutions.
Aim Integration also offers personal account access control that prevents privileged users from viewing sensitive data accessed or altered via Aim Integration accounts, real-time surveillance technology also enables real-time protection of secret histories by stopping suspicious or harmful activity before it does any lasting harm, providing real peace of mind that’s crucial when dealing with sensitive or potentially destructive activities!
Companies using CyberArk’s Aim Integration platform may experience improved security posture and operational efficiencies among other benefits.
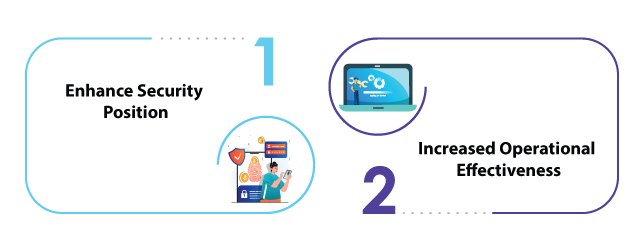
Enhance Security Position: Businesses can strengthen their security posture with CyberArk Aim Integration’s management, regulation, and monitoring of privileged accounts to protect digital assets against hacker threats while quickly responding to potential security concerns by quickly detecting suspicious and harmful behavior in privileged accounts.
Aim Integration also assists organizations in quickly responding to any potential security vulnerabilities with timely mitigation plans or solutions being put in place quickly if any arise.
Increased operational effectiveness: Businesses can enhance operational effectiveness while saving both time and money while devoting more attention and energy towards activities that provide true value to the bottom line.
Benefits of CyberArk
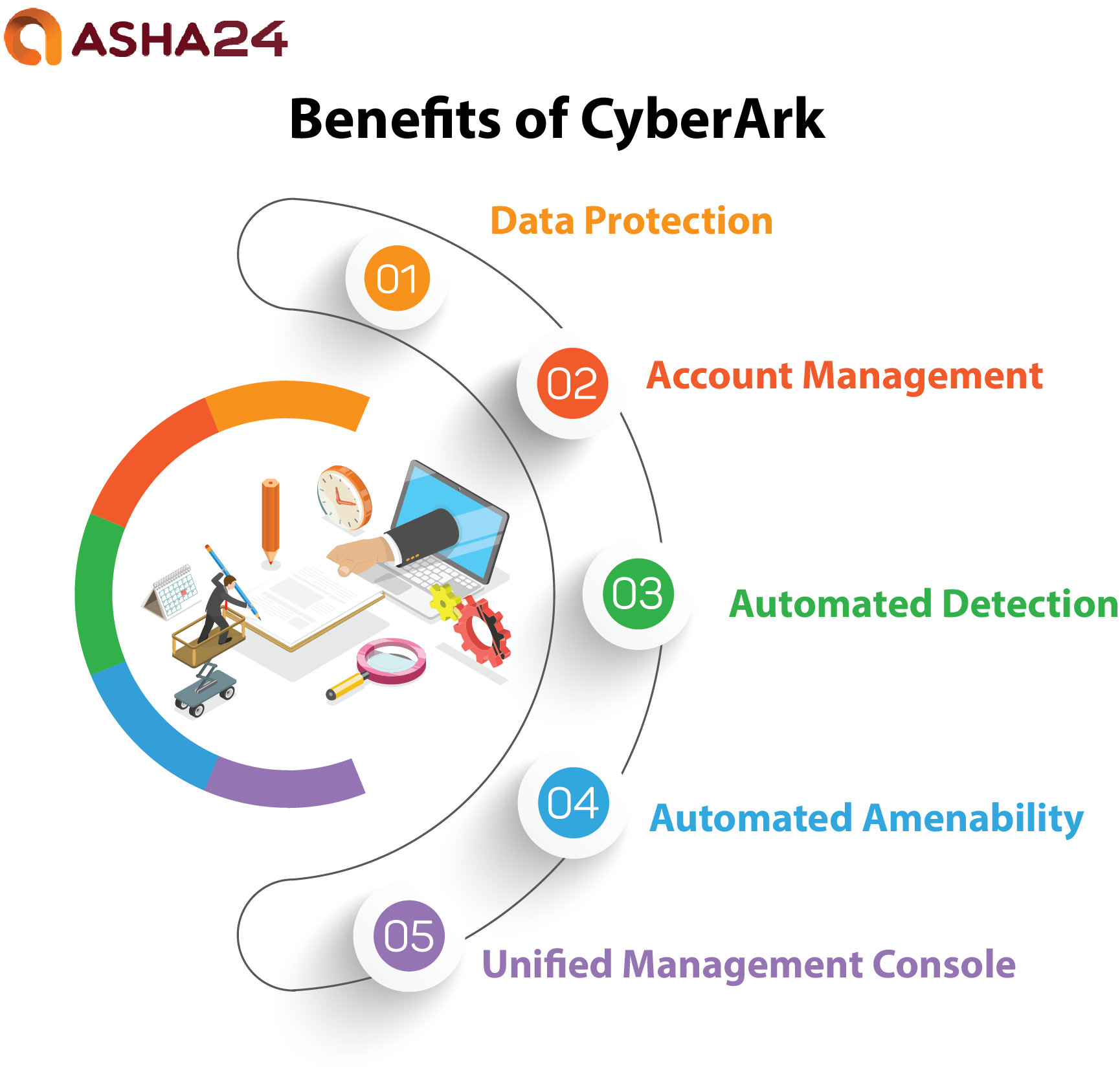
Data Protection: CyberArk’s cutting-edge identity and access control technologies make safeguarding personal data from internal and external threats possible, helping ensure only authorized individuals gain access to it.
Account Management: PAM solutions enable businesses to store and centralized control privileged accounts and high-risk access securely, offering an audit trail for each action taken with secret histories, helping identify any abuse of selective access privileges within organizations and prevent select access abuse in future.
Automated Detection: Its automated detection tools make it simpler than ever to identify accounts vulnerable or exposed to security risks, with real-time monitoring and alert messages providing continuous protection from security risks that might present themselves immediately.
Automated Amenability: Businesses may leverage CyberArk technologies to establish security policies and controls based on laws and industry norms, while organizations may ensure they satisfy relevant security criteria via automated reporting and audit procedures.
Unified Management Console: CyberArk’s Unified Management Console provides a central management interface for controlling an organization’s security systems, making it easier than ever before to identify and address security threats and issues from one place.
It makes it possible for users to securely access programs, services and data safely, helping increase overall workforce productivity overall by eliminating redundant log-ins and passwords and decreasing wasted time.
CyberArk Features
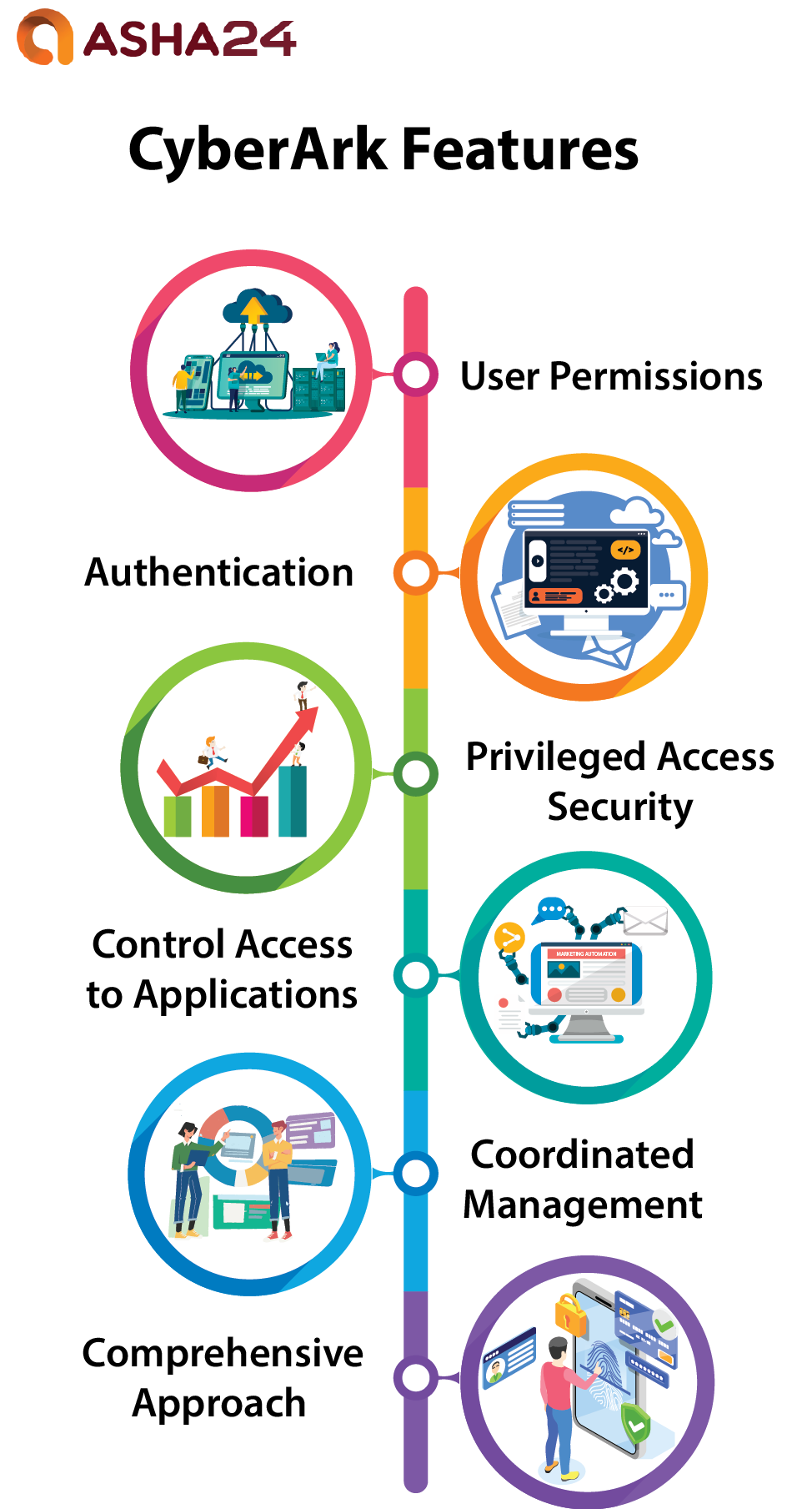
User Permissions: Organizations can implement user permission controls using CyberArk’s secure vault technology to implement finely tuned access control measures for critical information and resources, restricting their usage by only authorized staff.
Authentication: Organizations can select an optimal authentication mechanism for their environment thanks to CyberArk Privileged Access Security Solution’s wide variety of methods , biometrics, password vaulting and two-factor authentication are just a few options available , which enables them to ensure only authorized users gain entry to their system.
Privileged Access Security: It features advanced session administration features for real time monitoring of individual user sessions in real time, enabling administrators to swiftly identify and respond quickly in response to unapproved access or suspicious behaviors.
Control Access to Applications: CyberArk Privileged Access Security Solution provides organizations with control of accessing specific applications. Users only gain access to those they require for their jobs and ensure maximum efficiency is reached with every use of them.
Coordinated Management: Businesses using CyberArk Privileged Access Security Solution can centrally administer and oversee all their privileged accounts, making it simpler to identify suspicious behavior immediately and take remedial actions quickly as it provides a single pane of glass view into specific user activity.
Comprehensive Approach: Organizations can entrust CyberArk Privileged Access Security Solution with protecting vital systems, applications, and data against hacker assaults and unapproved access.
CyberArk features User Authorization and User Authentication which ensure only authorized personnel may gain entry while its secure vault technology serves to manage access control over sensitive resources and manage access permission for sensitive resources.
Asha24 offers comprehensive CyberArk training courses tailored specifically for novice and seasoned professional users alike, covering examples of best practices from experienced instructors as well as instructor-led live sessions or self-paced learning options with them.

Ankit
Author
Hola peeps! A fitness freak, a lover of games, I catch a flick on the weekends and write for you about current trends.