CyberArk Tool- Secure your business with this predominant security tool
Companies need to take action in order to safeguard their digital assets as Cyberattacks increase in frequency and sophistication. Leading cybersecurity software company CyberArk assists businesses by protecting both network access points as well as data from online attacks. Let us have a deep look into the technology in this CyberArk tool tutorial.
CyberArk Meaning
CyberArk is the global authority in solutions for privileged access security. Their secure platform protects an enterprise’s most critical user accounts, such as administrative accounts, secret user accounts, privileged application accounts, service accounts, and shared accounts – helping businesses avoid malicious activities like data theft, unauthorized access, and loss.
CyberArk’s platform is founded upon the defense-in-depth principle, giving clients a reliable layer of defense-in-depth security that allows them to monitor privileged access, detect threats quickly and respond efficiently to incidents promptly and efficiently.
CyberArk Privileged Access Security (PAS) offers comprehensive solutions to revolutionize how organizations secure, administer, and monitor privileged access.
The platform offers privileged access governance, password management, session management, audit and reporting capabilities, security policy automation, and application identity management.
It allows businesses to protect their most critical digital assets against possible attacks while mitigating risks related to an attack.
This solution aims to give organizations greater transparency and control of privileged access.
It offers secure onboarding/provisioning/approval steps and immediate reporting capabilities on privileged activities so organizations can quickly investigate root-cause situations or regulatory issues and take necessary measures.
It provides integrated detection and response capabilities to spot malicious activity quickly and respond with automated remediation or manual approvals when necessary.
Real-time profiling of user behavior, advanced analytics, and machine learning help identify threats on the CyberArk platform – helping businesses quickly detect any possible malicious activities.
CyberArk’s Privileged Access Security Solutions provide organizations with real-time visibility and control of all privileged access activities, providing visibility of select account activity to help protect networks against insider attacks from incidental users and malicious insiders.
Organizations may ensure that only authorized users have access to privileged accounts by regularly checking logs for any unusual activity.
Thus protecting networks against unauthorized or malicious access attempts. The platform even features anomaly detection functionality which detects any potentially illegal access attempts that might attempt unauthorized gains entry by unauthorized insider attacks from within.
It offers businesses:
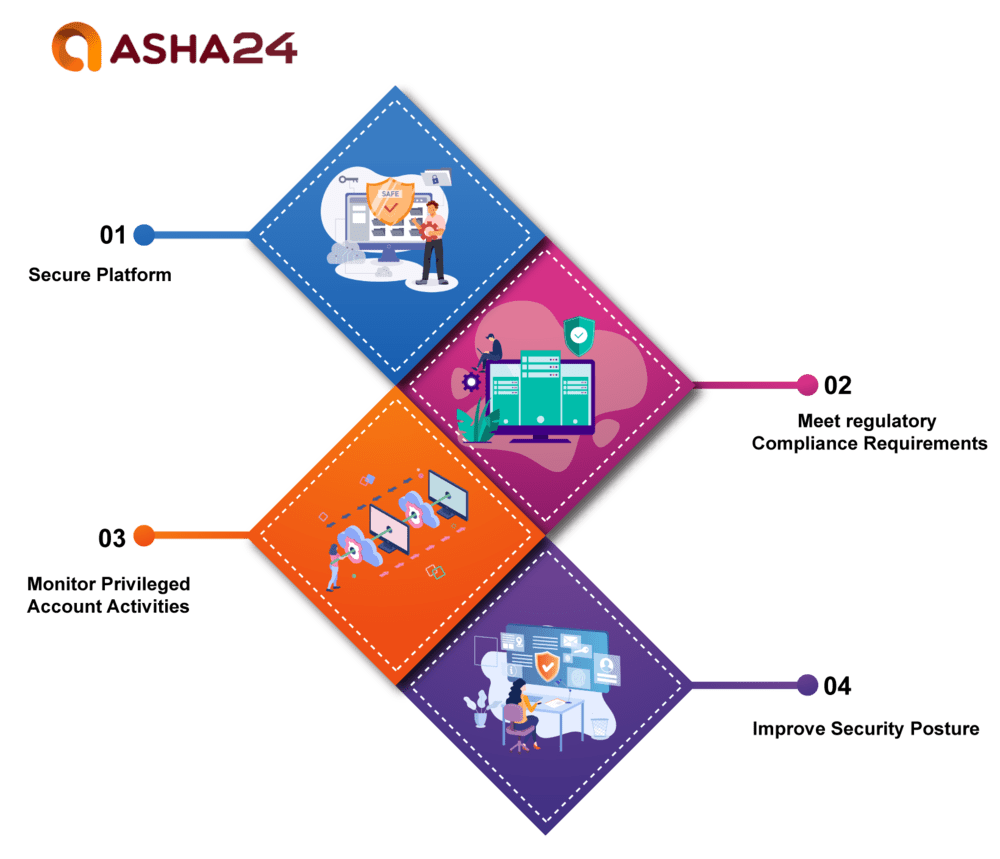
A secure platform to safeguard the most essential user accounts within their organization
Helping meet regulatory requirements,
Monitor privileged account activities, detect threats more effectively, and respond swiftly.
Improve overall security posture and protect networks against unapproved access and data loss.
CyberArk Architecture Overview
The CyberArk architecture is a multi-tier corporate privileged access security technology platform that protects privileged account credentials. This solution comprises these components:
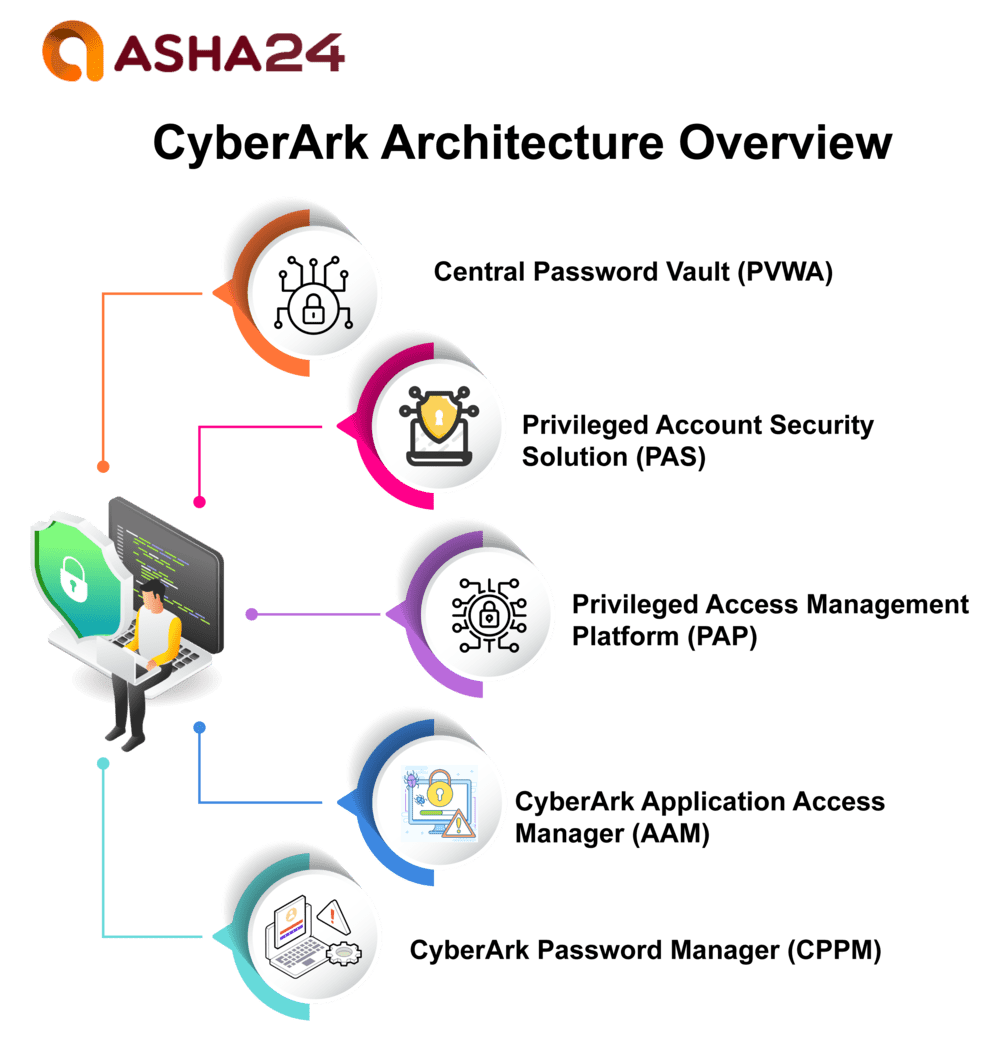
- Central Password Vault (PVWA): This vault is the central repository of privileged accounts, securely storing and managing all secret passwords. It supports various authentication methods and password rotation strategies, as well as audit logging for increased control over accessing these privileged accounts.
- Privileged Account Security Solution (PAS): PAS provides the essential solution for effectively overseeing and controlling privileged account access, acting as the secure access gateway with capabilities like authorization management, single sign-on support and access control management.
- Privileged Access Management Platform (PAP): PAP is an integrated platform designed to assist IT administrators and security teams with finding, protecting, monitoring and auditing of privileged accounts in real-time. This aid facilitates real-time account identification, protection and auditing.
- CyberArk Application Access Manager (AAM): With AAM’s web-based access and identity governance tool, organisations are able to efficiently issue, deprovision and monitor application user access in an efficient manner – offering an intuitive graphical workflow-based system for making access control decisions.
- CyberArk Password Manager (CPPM): CyberArk’s Password Manager provides organisations with a safe solution for securely storing, managing and controlling privileged account credentials. Featuring robust encryption technology with user authentication for data protection as well as remote secure password access using web client technology – its CyberArk benefits extend far beyond mere password storage.
CyberArk Benefits
Bellow are the list of CyberArk Benefits:
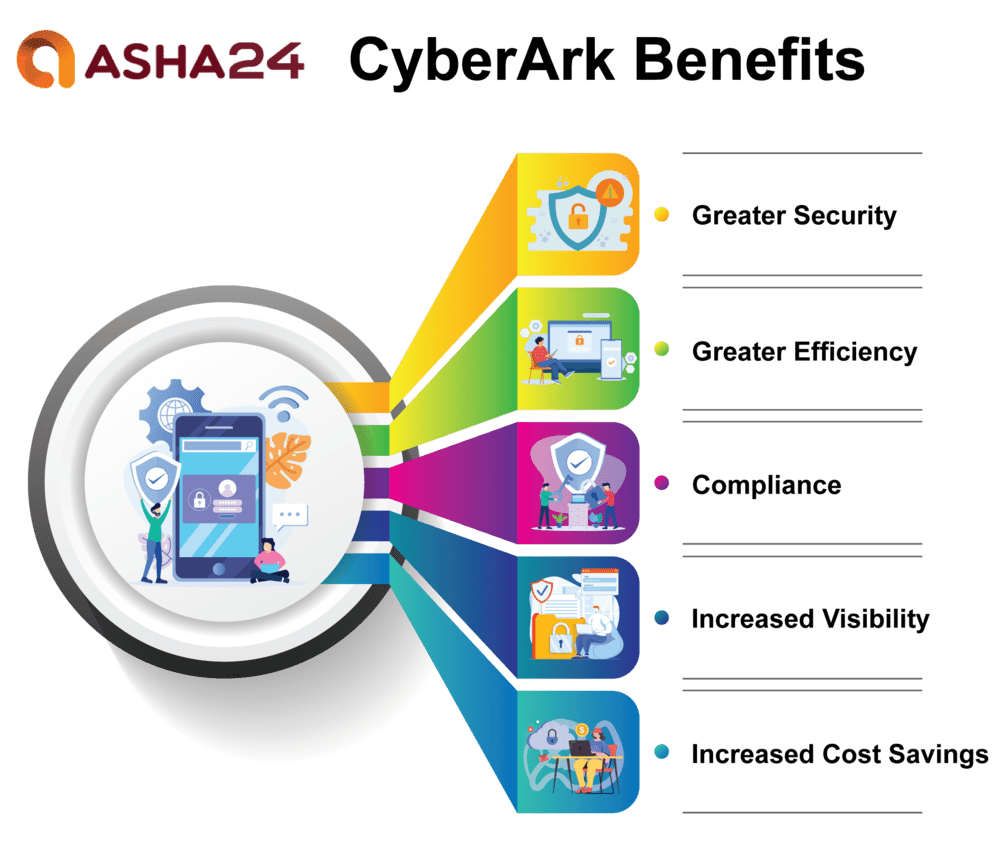
CyberArk offers several benefits to both businesses and their clients.
Greater Security: CyberArk’s cutting-edge enterprise security solutions protect businesses against sophisticated threats from criminal actors while at the same time shielding identity theft, malicious software installations and compromised infrastructures from damage and corruption.
Greater Efficiency: CyberArk offers integrated solutions, automation, and a decrease in manual operations, which help organisations simplify and streamline their security procedures. Organisations may then concentrate on other profitable operations with the time and resources saved as a result.
Compliance: CyberArk assists businesses in adhering to rules set out by Payment Card Industry Data Security Standard (DSS), other organizations and the government. With CyberArk technologies at their fingertips, businesses stay abreast of legislation while still staying compliant.
Increased Visibility: CyberArk provides network-wide visibility by tracking endpoints, malicious activity points, and credentials in real time to enhance situational awareness for businesses looking to understand better who has access to their networks and any vulnerabilities. This visibility helps businesses better comprehend who has access and any possible points of vulnerability within.
Increased Cost Savings: CyberArk helps businesses save operational expenses with its hosted and automated solutions that protect networks, data, and applications, while its SaaS business model reduces capital outlay required to set up and operate security systems.
CyberArk advantages
The following are the several advantages of CyberArk:
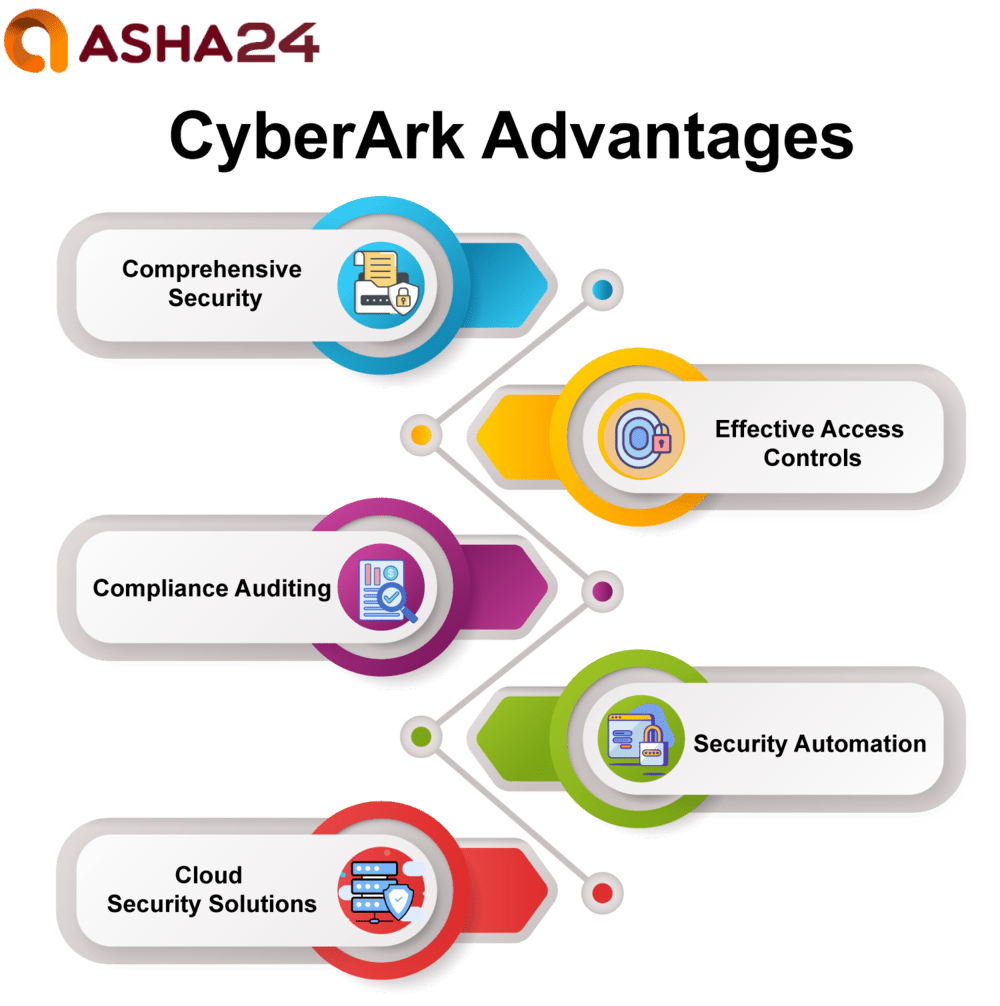
- Comprehensive Security: CyberArk offers comprehensive security tools designed to evaluate vulnerabilities, mitigate them effectively, detect them promptly, and audit for consent purposes. By offering an in-depth breakdown of hazards associated with each device or system it protects, CyberArk helps reduce risks while simultaneously guaranteeing consistency.
- Effective Access Controls: CyberArk’s access controls help restrict user access to sensitive information as well as system exploiters who attempt to gain unauthorized entry and exploit your system, helping identify and prevent harmful activity from taking place in your environment.
- Compliance Auditing: CyberArk’s auditing services offer businesses assistance in locating and mitigating security threats or concerns related to any system, making it simpler to ensure they’re meeting legal, regulatory, or sectoral standards.
- Security Automation: CyberArk’s automated security solutions are tailored to improve operations while minimising manual labour. Automation may assist in streamlining security procedures, enforcing policies more quickly, reacting faster when an incident arises and reporting security flaws more efficiently.
- CyberArk’s Cloud Security Solutions: These cloud security solutions from CyberArk aim to protect data and applications accessed over the cloud by helping ensure cloud service providers abide by regulations while taking precautionary steps against bad actors.
CyberArk integration
CyberArk Integration is an IT security service that keeps track of passwords in other IT systems and apps. It allows organizations to safely store, handle, and control privileged accounts and passwords for users, making entry more secure at the system level.
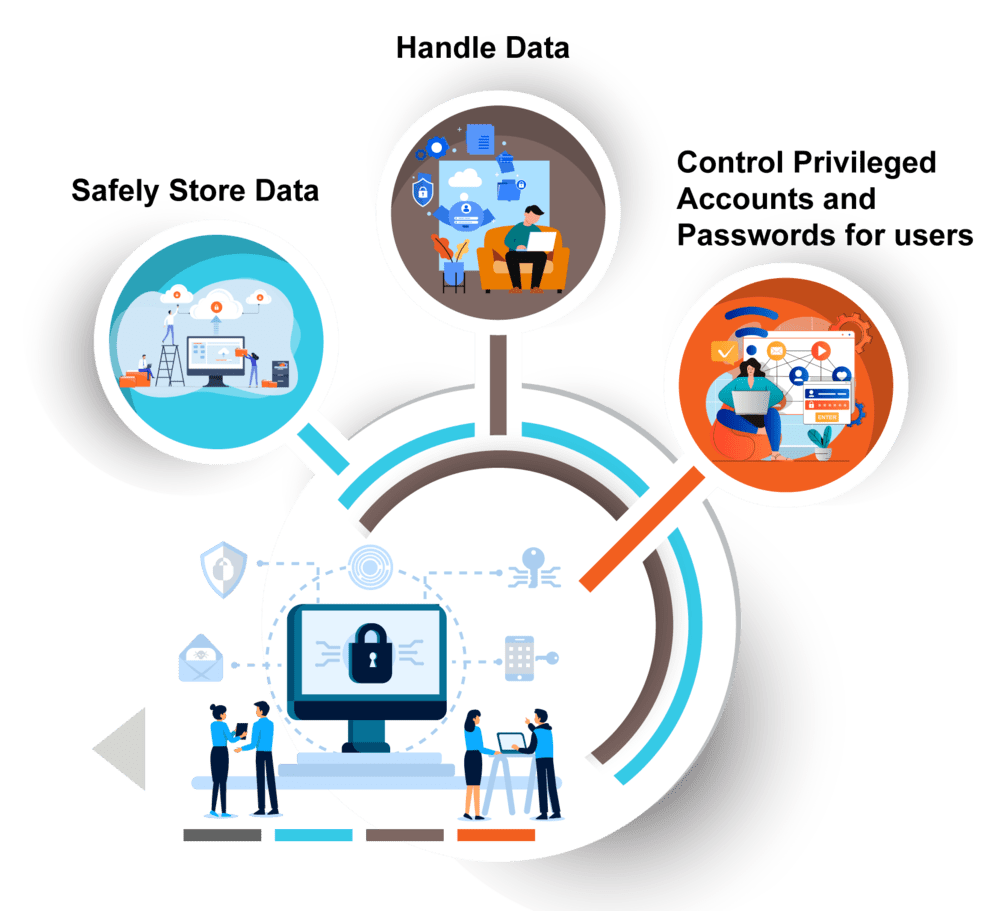
Users can be secure in accessing multiple apps with one set of credentials while setting access limits at the user level and keeping tabs on special sessions simultaneously with CyberArk integrated.
This interface also enables organizations to monitor what users are up to at any one time. It provides continuous oversight, allowing the organizations to keep tabs on special sessions that may arise by tracking what users are up to as they progress.
CyberArk jobs for freshers
CyberArk’s privileged access security solutions offer organizations enhanced protection from internal and external threats for mission-critical systems, applications, and data.
CyberArk helps businesses mitigate insider threats, negligence, and advanced persistent threats (APTs).
Furthermore, this software assists organizations in detecting, protecting, and monitoring privileged account access while improving regulatory and auditing capabilities.
CyberArk technology has many uses within organizations and is in high demand.

Understanding CyberArk will also assist with understanding endpoint security and how to implement safeguards to guard against external attacks.
Consequently, acquiring this technology could increase one’s employment prospects.
CyberArk opensource alternative
The following are the alternatives of Cyberark:
Saviynt
Sailpoint
Okta
Ping
ForgeRock
CyberArk Password Vault tutorial
The CyberArk Password Vault is an innovative, secure password storage system that empowers organizations to safeguard sensitive data while managing privileged accounts in on-premise, hybrid, and cloud settings.
Utilizing advanced encryption techniques, it safely stores private credentials ensuring maximum protection of sensitive information and accounts.
CyberArk Password Vault boasts multi-factor authentication, audit logging, and vulnerability scanning to ensure that only trusted individuals with valid credentials gain access to confidential data.
Because it offers one platform for all privileged access needs, CyberArk Password Vault is frequently employed for administering both user credentials and administrative secret accounts.
CyberArk PIM tutorial
CyberArk Privileged Identity Management (PIM) offers organizations security solutions for managing privileged accounts that allow them to monitor, protect, and track them across on-premises, cloud, and hybrid business environments.
Validate user access requests, report statuses and locate and protect privileged accounts automatically with single sign-on to entitlements ranging from single password vaults to multifactor security for special accounts with secure access—track and record sessions.
There are a variety of platforms where CyberArk tutorials, PDFs, and videos can be accessed. However, an online training platform is the ideal method to acquire vast knowledge.
I recommend Asha24 as the finest platform to participate in this regard.
Here you can find the finest CyberArk password vault tutorials, CyberArk PIM tutorials, CyberArk Pdfs, CyberArk Course materials, and content.
As an online training platform, this is accessible from anywhere, making it ideal for both students and working professionals.

Chandanakatta
Author